HIPAA
HIPPA
HIPAA 2024 Training Course
This course will cover the basic HIPAA rules for the use, transmission, security and privacy of healthcare data.
Note: This information is not legal advice. This information provided comes directly from the Health & Human Services who enforce and educate on HIPAA. The Office for Civil Rights is an agency within the HHS Department that enforces HIPAA. HIPAA can also be enforced by your State Attorney General.
HIPAA is all about protecting patient privacy. Use the guidelines within this course to help your organization protect patient information.
Course Outline
Section 1: What is HIPAA?
Section 2: What are the 5 Main Components of HIPAA?
Section 3: What information is protected under HIPAA?
Section 4: What is the Privacy Rule?
Section 5: What is the Minimum Necessary Rule?
Section 6: What rights do patients have under HIPAA?
Section 7: More on patient safety
Section 8: Emergency situations and law enforcement
Section 9: What is the Security Rule?
Section 10: What are Limited Data Sets?
Section 11: What are Cyber Security Requirements?
Section 12: HIPAA enforcement and audits
Section 13: What is a breach?
Section 14: How does HIPAA affect marketing?
Section 15: Managing and resolving HIPAA complaints
Section 16: What documentation is required under HIPAA?
Section 17: Cloud computing and Social Media
HIPPA Section 1

HIPPA is a Privacy and security Act that requires that anyone who comes into contact with Protected Health Information go through a training on HIPAA policy at least annually, and that there is documentation to prove that training was completed each year.
What does HIPAA stand for?
HIPAA stands for Health Insurance Portability and Accountability Act.
When was it created?
HIPAA was signed into law in 1996.
Why is HIPAA Needed?
There were no national requirements for protecting health information in the health care industry prior to HIPAA. In the mid-1990’s, technology was rapidly evolving, moving from paper to electronic for many administrative and clinical-based daily tasks.
With millions of records are compromised each year, most of which are due to poor handling of documents and electronic files, HIPAA was created to put policies and procedures in place to help organizations keep private healthcare data secure.
What businesses must comply with HIPAA laws?
Any healthcare entity that electronically processes, stores, transmits, or receives medical records, claims or remittances. The keyword here is electronic.
How does HIPAA affect you in your day-to-day job?
-Everyone has personal health information. Protecting this information is one of the most important duties of any healthcare professional not only because privacy is a right, but all because it is federal law and is therefore mandatory.
-It is important to understand the measures to take and procedures to follow, as part of your job responsibilities in the healthcare industry is to understand how to help keep patient information private and safe.
What do HIPAA requirements do?
-Protect the privacy of individual’s health information through its developed standards and requirements.
-Protect people from losing their health insurance if they change jobs or have pre-existing health conditions.
-Reduce costs and administrative burdens of healthcare by creating standard electronic formats for many administrative transactions that are currently completed via paper.
-Provide covered organizations the ability and guidelines for implementing new technology to better safeguard private information.
Who enforces HIPAA?
-The Department of Health and Human Services, OCR Division, is responsible for enforcing fines and violations.
-Millions of dollars in HIPAA fines are issued each year. HIPAA fines for privacy violations, like most government fines, continue to increase.
Is HIPAA updated?
Yes, HIPAA has been updated several times since its inception in 1996. HIPAA updates are made frequently through guidance notices issued by HHS Office for Civil Rights (OCR) to account for advances in technology and changes to working practices. For this reason, HIPAA requires each healthcare professional to review HIPAA requirements at least on an annual basis.
Notable updates include:
-The HITECH Act of 2009
With this rule, penalties were increased for non-compliance. It also imposed strict requirements for data breaches including investigating, reporting and implementing improvements, if any.
-The Final Omnibus Rule of 2013
With this rule, HIPAA strengthened privacy protection to its greatest level yet, including setting new limits on how information is used and disclosed for marketing and fundraising purposes, and also prohibiting the sale of an individual's health information without their permission.
HIPPA Section 2
What are the 5 Main Components of HIPAA?
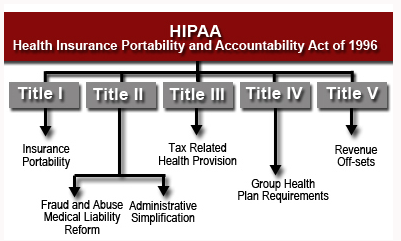
The 5 main components of HIPAA are:
Title I.
Allows individuals to maintain their coverage when employment changes and the individual is on a group plan. In addition, Title I makes it illegal for group insurance plans to deny individuals who they do not want to cover, including the building of lifetime maximums into contracts.
Title II.
The U.S. Department of Health and Human Services (HHS) establishes national standards for processing electronic healthcare transactions and requires healthcare organizations to implement secure electronic access to health data and to remain in compliance with privacy regulations set by The U.S. Department of Health and Human Services.
Title III.
Updated tax rules regarding healthcare treatment.
Title IV.
More details on the reform of insurance law, protecting individuals with pre-existing conditions and also individuals who want to maintain their insurance.
Title V.
Provides guidelines for life insurance policies owned by businesses, including situations for handling income taxes when US citizenship is revoked for individuals.
Title II is the section of HIPAA for IT providers, and those who process, store or transfer health data. This part of the law is also called The Administrative Simplification Provisions.
Title II has the following 5 components:
1) Privacy Rule – Also known as The Standards for Privacy of Individually Identifiable Health Information, this rule outlines the patient health information that must be protected, along with best practices.
2) Security Rule – Also known as The Security Standards for the Protection of Electronic Protected Health Information, this rule details safeguarding requirements of patient data, along with best practices.
3) Enforcement Rule – Investigations and rulings for HIPAA Violations.
4) National Provider Identifier Standard – 10-digit NPI (national provider identifier) numbers must be assigned to all healthcare entities.
5) Transactions and Code Sets Standards – An objectively approved protocol must be used in electronic data interchange (EDI).
HIPPA Section 3
What information is protected under HIPAA?

Health information that can be connected to a person is protected under HIPAA.
What is PHI?
PHI stands for Protected Health Information.
Protected information includes personal information such as:
-Social Security Number
-Name
-Address
-Date of Birth
Personal information also covered under HIPAA includes:
-Past, present or futures health conditions
-How the healthcare was provided
-The payment history for the healthcare
-Billing information
How is this information covered?
HIPAA covers the protection of this information when it is used or disclosed orally, written, printed on paper, or submitted electronically.
What is the best practice when dealing with health information?
The best practice when dealing with health information is to assume it is protected by HIPAA until you are told differently by a HIPAA expert.
Who is covered under HIPAA?
Doctors, all healthcare providers Insurance plan providers, claim processors, clearing houses and patients are covered under HIPAA.
Organizations covered by HIPAA are called Covered Entities.
A covered Entity is any organization or individual who has access to patient records.
These include:
-Healthcare providers
-Health plans
-Healthcare clearinghouses
-Business associates
What are the HIPAA requirements of a covered entity?
A covered Entity must provide written safeguards that detail PHI use to business associates upon hiring.
The business associate is then subject to the same HIPAA rules (as any other covered entity) and cannot be (contractually) authorized to violate the HIPAA rule.
How is protected health information protected?
In many cases, authorization from a patient or patient’s family is required in order to use or disclose patient PHI.
When is permission to disclose PHI NOT required?
-HIPAA was never intended to get in the way of prompt and effective medical care.
-There are several scenarios where this authorization is not required:
-When treating a patient, the full records of an individual’s medical history is needed in order to provide the best care possible. Therefore, permission is not needed when PHI is accessed by professionals directly involved with the patient’s medical care.
-No permission is needed to use and disclose PHI for Healthcare operations and billing. Healthcare workers would receive PHI in these instances, should do everything in their power to keep the information private.
What is incidental exposure?
Incidental exposure involves situations where keeping information private is not possible. Medical professionals should take reasonable care to keep information private.
For example, when discussing treatment and care of a patient, avoiding public areas like waiting rooms or elevators. If this is not possible, avoid using patient names.
Another example: If a patient is not in a private room, the curtains should be pulled closed and reasonable attempt to not be overheard should be made.
HIPPA Section 4
What is the Privacy Rule?

The Privacy Rule generally requires covered entities to take reasonable steps to limit the use or disclosure of, and requests for, protected health information to the minimum necessary to accomplish the intended purpose.
-Privacy Rule compliance requirements
Privacy Notice
The HIPAA Privacy Rule requires health plans and covered health care providers to develop and distribute a notice that provides a clear, user friendly explanation of individuals rights with respect to their personal health information and the privacy practices of health plans and health care providers.
HHS created templates for both health plans and health care providers and has made them available for download.
Who is the Privacy Official and what are their responsibilities?
The Privacy Rule requires the following administrative safeguards to ensure that PHI is not compromised:
-A Privacy Officer
Designating a Privacy Officer to be responsible for the development and implementation of privacy policies and the receiving of complaints.
-Training
Training of all workforce members on privacy policies and procedures, as necessary and appropriate for them to carry out their job functions.
-Business Associates
Requiring business associates such as lawyers, consultants, auditors, billing companies and pharmacists to confirm that they will protect PHI.
-Tracking
Developing a system that will track who accessed what information.
-Violations
Implementing rules for addressing violations of privacy, security and transaction regulations, including establishing a process for making complaints and preventing retaliation against anyone who reports a HIPAA violation.
HIPPA Section 5
What is the minimum necessary rule?

The Minimum Necessary Rule is a key protection of the HIPAA Privacy Rule. It calls for using the minimum amount of PHI necessary to get the job done.
This is also referred to as Access Controls to ensure that access to sensitive information is available on a need-to-know basis, based on user responsibilities.
As an example, doctors and nurses, who are directly involved with the treatment of a patient, need all of the patient’s medical history available in order to provide effective medical care.
But, other workers involved in the care, lab technicians for example, need only a small amount of the patient’s personal health information.
Covered entities need to establish policies and procedures that restrict the access and use of PHI to the minimum level of PHI necessary.
Employees who regularly access PHI need to be categorized by the type of PHI they need and the condition for their access so that only the amount of information they need to do their job effectively is released.
What are reasonable safeguards?
Covered entities are required to have appropriate administrative, physical and technical safeguards in place to protect against the disclosure and usage of PHI not permitted by the Privacy Rule. These safeguards must also limit incidental uses or disclosures.
While safeguards will not guarantee the privacy of protected health information from all potential risks, they must exist. Reasonable safeguards will differ based on several factors including the covered entities size and business nature.
Covered entities will need to analyze their circumstances and needs, including the type of the protected health information it maintains, and assess the potential risks to patient privacy when implementing reasonable safeguards. There are other considerations when implementing safeguards, including administrative and financial burdens.
Many health care providers and professionals have policies in place to ensure reasonable safeguards for patient health information, including the following:
-Speaking quietly when discussing a patient’s condition with family members in a waiting room or other public area
-Avoiding using a patient's name in public elevators and hallways, while also posting signs to remind employees to protect patient confidentiality
-Isolating or locking file cabinets or records rooms
-Providing additional security on all computers maintaining personal information such as passwords.
Technical safeguards are also required under HIPAA and include:
-Audit Controls
To record and examine system activity to help eliminate unnecessary access to sensitive information.
-Data Authentication
Controls to help ensure that health data has not been altered in an unauthorized manner.
-Person or Entity Authentication
Controls to ensure that data is sent to the intended recipient and received by the intended party. These controls include the use of password protections, PIN numbers and, when sent over public networks, encryption.
-Transmission Security
Sending PHI via E-mail and Fax.
In addition to patient treatment, operations, and billing, there are several other scenarios where no permission is needed to release the minimum necessary PHI.
These scenarios include:
-For public health activities relates to disease prevention and control.
-To report victims of abuse, neglect or domestic violence.
-For audits, legal investigations, licensure, law enforcement purposes and government functions.
-For coroners, medical examiners, funeral directors, tissue organ donations and certain research purposes.
-Requests from employers for work-related illness, injury or medical surveillance to comply with OSHA, MSHA or a similar state law.
-To avert a serious threat to health and safety.
-And as a limited data set where all personal identifiers have been stripped out.
Minimum Necessary PHI can also be used or disclosed without authorization to:
-Maintain a patient directory.
-Inform family members about care, location, condition or death.
-Inform agencies during disaster relief.
These are accomplished by getting simple verbal consent from the patient.
More on Consent
For example, it is usually permissible to release information on the patient’s progress to family or friends who accompanied the patient to the hospital,
However, if a family member arrives after the patient’s admission, it is important to check identification and to review the facts of the case before proceeding, especially if there is evidence of domestic violence or abuse.
It is important to remember that after consent is given to give information to the patient’s family, it must be done so privately so that no one else can easily overhear.
What are the HIPAA rules regarding disclosing protected information over the telephone?
HIPAA allows for healthcare providers to communicate with patients by phone or mail.
When leaving a message or with a family or other person when the patient is not at home, leave the minimum amount of information necessary. Leave only your name and phone number and ask for a call back or leave the minimum amount of information necessary to confirm an appointment.
HIPPA Section 6
What rights do patients have under HIPAA?
The Privacy Rule generally requires HIPAA covered entities to provide individuals with, when requested, access to their PHI in one or more designated record sets that are maintained by or for the covered entity.
Included is the right to inspect and/or obtain a copy of their PHI, and also to direct the covered entity to send a copy to a designated person or entity of the individual’s choice. Individuals have a right to access their PHI for as long as the information is maintained by a covered entity or business associate on behalf of a covered entity, regardless of:
-The date the information was created
-Whether the information is maintained in paper or electronic systems onsite, remotely, or is archived
-Where the PHI originated (covered entity, the patient, another provider, etc.).
The information that is included in the Right of Access: the “Designated Record Set”
Individuals have the right to access PHI in a designated record set. A designated record set is defined as a group of records maintained by or for a covered entity that encompasses the following:
-Medical records and billing records about individuals, maintained by or for a covered health care provider
-Enrollment, claims outcome, payment, and case or medical management record systems maintained by or for a health plan
-Other records used by or for the covered entity to make decisions about the individual, including records that are used to make decisions about any individuals, whether or not the records have been used to make a decision about the particular individual requesting access.
A “record” is defined as any item, collection, or grouping of information that includes PHI and is maintained, collected, used, or disseminated by or for a covered entity.
Individuals have a right to a wide range of health information about themselves that are maintained by or for covered entities. This includes the following:
-Billing and payment records
-Clinical laboratory test results
-Clinical case notes
-Insurance information
-Medical images, such as X-rays
-Medical records
-Wellness and disease management program files
-Additional information used to make decisions about the individual.
A covered entity is not required to create new information, such as explanatory materials or analyses, if it does not already exist in the designated record set, when responding to a request for access.
Information not included in the Right of Access
Individuals do not have a right to access PHI that is not part of a designated record set because the information is not used to make decisions about the individual. This information includes certain quality assessment or improvement records, patient safety activity records, or business planning, development, and management records used for business decisions more generally than for making decisions about individuals.
As an example, a hospital’s staff performance or quality control evaluations used to improve customer service can be generated and include an individual’s PHI but might not be in the covered entity’s designated record set and subject to access by the individual.
Two additional categories of information are excluded from a patient’s right of access:
- Psychotherapy personal notes of a mental health care provider that document and/or analyze the contents of a counseling session maintained separate from the rest of the patient’s medical record.
- Information assembled in anticipation of or for use in an administrative, civil or criminal action or proceeding.
Note that the PHI from the individual’s medical or payment records or other records used to generate the above types of excluded records or information remains part of the designated record set and subject to access by the individual.
Personal Representatives
Upon request, an individual’s personal representative has the right to access PHI about the individual in a designated record, provided it is consistent with the scope of such representation.
Requests for Access
Requiring a Written Request
A covered entity can require individuals to request access in writing as long as the covered entity informs individuals of this requirement. Covered entities can also offer individuals the option to make requests for access electronically. A covered entity can also require individuals to use the entity’s own supplied form as long as the use of the form does not create a barrier to the individual obtaining access to their PHI and does not create unreasonable delays.
Verification
The Privacy Rule requires a covered entity to take reasonable steps to verify the identity of an individual making a request for access. The Rule does not mandate a specific form of verification, but leaves the type and manner of the verification to the discretion of the covered entity, provided the verification processes and measures do not create barriers to or unreasonably delay the individual from obtaining access to their PHI.
Verification may be done orally or in writing and, in many cases, the type of verification may depend on how the individual is requesting and/or receiving access – whether in person, by phone (if permitted by the covered entity), by faxing or e-mailing the request on the covered entity’s supplied form, by secure web portal, or by other means.
As an example, if the covered entity requires that access requests be made on its own supplied form, the form could ask for basic information about the individual that would enable the covered entity to verify that the person requesting access is the subject of the information requested or is the individual’s personal representative.
For those covered entities providing individuals with access to their PHI through web portals, those portals should already be set up with appropriate authentication controls to ensure that the person seeking access is the individual or the individual’s personal representative.
Unreasonable Measures
While the Privacy Rule allows covered entities to require that individuals request access in writing and requires verification of the identity of the person requesting access, a covered entity cannot impose unreasonable measures on an individual requesting access that serve as barriers to or unreasonably delay the individual from obtaining access. For example, a doctor cannot require an individual to:
-Physically come to the doctor’s office to request access and provide proof of identity in person, if the patient wants a copy of their medical record mailed to their home address.
-Use a web portal for requesting access.
-Mail an access request.
Covered entities are encouraged to offer individuals multiple options for requesting access.
Providing Access
Form and Format and Manner of Access
The Privacy Rule requires covered entities to provide an individual with access to their PHI in the form and format requested if readily available in that form and format.
If the individual requests electronic access to PHI that the covered entity maintains electronically, the covered entity must provide the individual with access to the information in the requested electronic form and format, if it is readily producible in that form and format, or if not, in an agreed upon alternative, readable electronic format.
Requests for Paper Copies
The covered entity will be able to provide the individual with the paper copy when an individual requests a paper copy of PHI maintained by the covered entity either electronically or on paper.
Requests for Electronic Copies
If an individual requests an electronic copy of PHI that a covered entity maintains only on paper, the covered entity is required to provide the individual with an electronic copy if it is readily producible electronically and in the electronic format requested if readily producible in that format, or if not, in a readable alternative electronic format or hard copy format as agreed to by the covered entity and the individual.
The covered entity also may provide the individual with a summary of the PHI requested instead of access to their PHI, or may provide an explanation of the PHI to which access has been provided in addition to that PHI, as long as the individual in advance chooses to receive the summary and agrees to any fees that are allowed to be charged by the covered entity for the summary or explanation.
Timeliness for providing access
When providing access to an individual, a covered entity must provide access to the PHI requested no later than 30 calendar days from the date of receiving the individual’s request.
The covered entity may extend the time by no more than an additional 30 days if a covered entity is unable to provide access within 30 calendar days. Within the initial 30 days, the covered entity must notify the individual in writing of the reasons for the delay and the date when the covered entity will provide access. One extension is permitted per access request.
HIPPA Section 7
More on Patient Safety
What is the Patient Safety and Quality Improvement Act?
The Patient Safety and Quality Improvement Act of 2005 (PSQIA) establishes a voluntary reporting system created to enhance the data available to assess and resolve patient health and safety care quality issues.
PSQIA provides Federal privilege and confidentiality protections for patient safety information referred to as patient safety work product, to encourage the reporting and analysis of medical errors.
PSQIA authorizes HHS to impose civil money penalties for violations of patient safety confidentiality.
PSQIA also authorizes the Agency for Healthcare Research and Quality (AHRQ) to list patient safety organizations, otherwise known as PSOs, who are the external experts that collect and review patient safety information.
What is the Patient Safety Rule?
The Patient Safety Rule was created in November, 2008 and implements some provisions of PSQIA.
This rule is also referred to as The Patient Safety and Quality Improvement Final Rule, and creates guidelines for health care providers that include doctors and hospitals, to voluntarily report information to Patient Safety Organizations (PSOs) and do so confidentially for the purpose of aggregation and analysis of patient safety events. Safety events provide an opportunity for all personnel to have a detailed discussion of methods for identifying errors and safety quality problems.
What is Signed Patient Authorization?
As a public entity, permission is needed before sensitive information can be given to anyone outside of your patient’s healthcare team.
This permission is granted by patients through an authorization form. To comply with HIPAA, it must be signed by the individual and include the date the document was signed in order to be valid.
E-signatures are allowed, provided they are part of a legally binding contract and Proper security safeguards are in place to verify the patient’s identity.
What is Patient control?
HIPAA provides the right for an individual to access their medical records.
HIPAA also provides individual with the option to consent to disclosure of their PHI for certain purposes including marketing.
Though HIPAA does not allow individuals to correct their medical records, they have the right to “amend” their records through adding in additional information.
What is the personal representative?
The personal representative is someone who can make health care decisions on behalf of an individual by using a health care power of attorney.
HIPAA-covered Health plans and health care providers in general must allow the personal representative to inspect and receive a copy of protected health information about the individual that are maintained by these entities.
An individual may name a Personal Representative in several ways. It is important to note that state law may affect this process.
-For children, the personal representative of a minor child is normally the child’s parent(s) or legal guardian, though state law can affect guardianship. The personal representative is the parent(s) who can make health care decisions for the child under the custody ruling, for situations where a custody ruling exists.
-For deceased persons, the personal representative is the administrator of the deceased individual’s estate. It can also be the person who is legally authorized by state law or a court to act on the behalf of the deceased individual or their estate.
-Exceptions exist, including a plan or provider having the ability to opt to not treat a patient through the personal representative if the plan or provider feel that the person may endanger the individual. Common reasons for this action include abuse, domestic violence and neglect.
HIPPA Section 8
Emergency Situations and Law Enforcement

What are HIPAA regulations regarding Emergency Situations?
The health care provider should get verbal permission from individuals, but if the individual is incapacitated or not available, covered entities will have to rely on their professional judgement to determine what is in the best interest of the patient in emergency situations where the patient is unresponsive or unable to consent.
Providers may share information in these instances if, in their professional judgement, doing so is in the patient's best interest.
When necessary, the hospital may notify the police, the press, or the public at large to the extent necessary to help locate, identify, or otherwise notify family members and others as to the location and general condition of their loved ones.
It is not necessary for a health care provider to obtain a patient's permission to share information if doing so would interfere with a disaster relief organization such as the American Red Cross’ ability to respond to the emergency.
When a patient may be facing imminent danger, providers can share patient information with anyone, as necessary, to prevent or lessen a serious, imminent threat to the safety and health of a person or of the public, provided it is done so consistent with applicable law and the provider's standards of ethical conduct.

What exceptions are there for law enforcement requests?
HIPAA defines law enforcement as “any government official at any level of government authorized to either investigate or prosecute a violation of the law.”
Under HIPAA, medical information can be disclosed to law enforcement officials without an individual’s permission in a several ways. Disclosures for law enforcement purposes apply to health plans, pharmacies, health care clearinghouses, and medical research labs, in addition to doctors or hospitals. These law enforcement access rules are required for covered entities and all business associates under the HITECH Act as implemented by the HIPAA Omnibus Rule.
HIPAA allows the police to use a written request such as an administrative subpoena, with no court involvement, provided the police include a written statement that de-identified information is insufficient, and that the information needed is limited in scope, relevant, and material.
Law enforcement has the ability to bypass administrative and judicial processes under HIPAA in order to get access to medical records. For example, the police may request medical information directly to identify or locate a missing person, witness, suspect or fugitive. In addition, medical information the police can request medical information when there is a medical emergency involved in a crime, when a crime has been committed at a health care facility. For the most part, these are all permissive disclosures covered entities and business associates can refuse.
Information including name, address, date of birth, place of birth, blood type, Social Security number, Rh factor, type of injury, date of treatment, time of treatment, date of death, time of death and any other distinguishing physical characteristics can be disclosed about a suspect or victim of a crime.
Information that requires a warrant, court order or written administrative request include body fluid, tissue type other than blood type samples and/or analysis, dental records, and DNA test results.
What is mandatory to report to law enforcement?
Every state requires that health care providers report child abuse or neglect. Most states require the reporting of elder abuse and neglect.
Aside from the four states of Alabama, New Mexico, Washington, and Wyoming, each state have law for mandatory reporting of domestic violence injuries and sexual assaults that are treated in health care facilities. It is important to note the laws they vary regarding who must report, the data they must report, and which agency or agencies they must report to.
Psychiatrists, psychologists and other licensed professionals may be required through ethical standards or law to report individuals to law enforcement they feel are likely to commit a violent crime.
HIPPA Section 9
What is the Security Rule?
The Security Rule requires covered entities to maintain reasonable and appropriate administrative, technical, and physical safeguards for protecting e-PHI (Electronic Personal Health Information).
Covered entities are required to:
-Ensure the confidentiality of e-PHI not being made available or disclosed to unauthorized persons, integrity, and availability of all e-PHI an organization creates, receives, maintains or transmits
-Identify and protect against reasonably anticipated threats to the security or integrity of the information
-Protect against reasonably anticipated, impermissible uses or disclosures
-Ensure compliance by their workforce
Who is the HIPAA Officer?
Also referred to as a HIPAA Compliance Officer, they are a Privacy Officer and a Security Officer. Anyone can be designated as the HIPAA Officer.
The duties of a HIPAA Compliance Officer can be divided between a Privacy Officer and a Security Officer. The same person can also be both.
What does the Security Rule require?
-A Security Officer
Designates a Security Officer to be responsible for the development, implementation and evaluations of security policies.
This may be the same person as the Privacy Officer.
-Risk Analysis
A technical evaluation and implementation of procedures to ensure that computers are secure from intrusion.
-Risk Management
Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with HIPAA requirements.
-A Sanction Policy
Applying appropriate sanctions against employees who fail to comply with HIPAA policies and procedures.
-Information System Activity Review
Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.
-Employee Security
Develop a plan for granting and limiting different levels of access to PHI, including clearance procedures and termination procedures.
-Employee ongoing training
This includes security checks and special training for all employees who have access to sensitive information.
Reminders that employees report incidents regarding PHI
Ensuring employees understand password security, computer virus protection, and the dangers of malicious software.
Also included must be
-A Contingency Plan
A plan for responding to system emergencies, including the performance of backups, emergency-mode operations, and disaster-recovery procedures.
-Security Incident Procedures
Instructions for reporting and dealing with security breaches.
Physical Safeguards are also required. These include:
-Facility Access Controls
Develop a facility security plan that deters intruders from accessing environments where sensitive information resides.
-Guidelines on workstation use and security
Procedures describing the proper function to be performed on computers, and how to handle sensitive information that may be displayed on computer screens.
-Media Controls
A set of procedures that govern the receipt and removal of hardware and software, such as disks, memory sticks, laptops, and PDAs, as well as, procedures for off-site data backup.
What is the HITECH Expansion of HIPAA?
Also referred to as the Hitech Act of 2009, the responsibilities of business associates under the HIPAA Security Rule were expanded. Potential legal liability was increased for non-compliance, along with more stringent enforcement. HHS developed regulations to implement and clarify these changes.
What is the HIPAA Final Rule?
The Final Rule, as required by the HITECH Act, applies the Security Rule as well as the majority of the Privacy Rule to Business Associates in the same way that the rules apply to Covered Entities. Many companies who were not regulated by HIPAA now fall under the enforcement authority of The U.S. Department of Health and Human Services, therefore facing direct liability for uses and disclosures of PHI not in accord with their Business Associate Agreements or the Privacy Rule, as a result.
HIPPA Section 10
What are Limited Data Sets?
Limited Data Sets under HIPAA is a set of identifiable healthcare information the HIPAA Privacy Rule allows covered entities to share with certain entities for healthcare operations, public health activities and research purposes without the need to obtain prior authorization from patients, but certain conditions need to be met.
While de-identified protected health information is no longer classified as PHI under the HIPAA Rules, a limited data set under HIPAA is PHI and subject to the HIPAA Privacy Rule regulation.
HIPAA limited data sets must be shared only with entities who have signed a data use agreement with the covered entity. This data use agreement allows covered entities to obtain satisfactory assurances that the PHI will be used only for specific purposes. It also assures the PHI will not be disclosed by the entity that it is shared with, and that the requirements of the HIPAA Privacy Rule are adhered to.
The data use agreement must be accepted before the limited data set is shared and should include the below information:
-Uses and disclosures allowed
-List of approved recipients and users of the data
-Agreement that data will not be used to contact or re-identify individuals
-Require the implementation of safeguards to ensure confidentiality of the data and to prevent prohibited use and disclosure of data
-Statement that the discovery of improper uses and disclosures of data must be reported back to the covered entity
-Statement that subcontractors who need to access or use the data enter into a data use agreement and also that they agree to comply with all requirements.
The HIPAA minimum necessary standard applies, while all information in the data set must be limited to only the information necessary to perform the purpose that it is disclosed for.
What Information needs to be removed from a Limited Data Set under HIPAA?
A limited data set cannot contain any of the following information:
-Name
-Street address or postal address information accept for town/city, state and zip code
-Phone and Fax number
-E-mail address
-Social Security number
-Medical records number
-Health plan beneficiary number
-Other account numbers
-Certificate and license numbers
-Vehicle identifiers and serial numbers, including license plate
-Device identifiers and serial numbers
-URLs and IP addresses
-Biometric identifiers such as fingerprints, retinal scans and voice prints
-Full face photos and comparable images
HIPPA Section 11
What are Cyber Security Requirements?

The HHS, Office for Civil Rights (OCR) provides steps for a HIPAA covered entity or its business associate to better understand how to respond to a cyber-related security incident and the steps to take if experiencing a cyber-related security incident.
If your entity experiences a ransomware attack or other cyber-related security incident, the steps for a HIPAA covered entity or its business associate (the entity) to take are as follows:
The covered entity or its business associate must execute its response and mitigation procedures and contingency plans. As an example, the entity should immediately fix any technical or other problems to stop the incident, while taking steps to mitigate any impermissible disclosure of protected health information, which may be done by either the entity’s information technology staff or by an outside entity brought in to help. Outside entities would be a business associate if it has access to PHI.
The covered entity or its business associate should report the crime to other law enforcement agencies. Agencies may include local or state law enforcement, the FBI and the Secret Service. These reporting should not include PHI unless permitted under the HIPAA Privacy Rule. If a law enforcement official tells the entity that any potential breach report would impede a criminal investigation or harm national security, the entity must delay reporting a breach for the time the law enforcement official requests in writing, or for 30 days, if the request is made orally.
The covered entity or its business associate should report any cyber threat indicators to federal and information-sharing and analysis organizations (ISAOs), including the Department of Homeland Security, the HHS Assistant Secretary for Preparedness and Response, and private-sector cyber-threat ISAOs. PHI should not be included in the reports.
The covered entity or its business associate must report the breach directly to the OCR as soon as possible and no later than 60 days after the discovery of a breach if it affects 500 or more individuals. Affected individuals and the media much be notified unless a law enforcement official has requested a delay in the reporting. The OCR assumes all cyber-related security incidents where protected health information was accessed, acquired, used, or disclosed are reportable breaches unless the information was encrypted by the entity at the time of the incident or the entity determines, through a written risk assessment, that there was a low probability that the information was compromised during the breach.
An entity who discovers a breach affecting fewer than 500 individuals has an obligation to notify individuals without unreasonable delay of no later than 60 days after discovery, and the OCR within 60 days after the end of the calendar year in which the breach was discovered.
OCR considers all mitigation efforts taken by the entity during a breach investigation. The efforts include covered entities or its business associates voluntarily sharing breach-related information with law enforcement agencies and other federal and analysis organizations mentioned above.
Ransomware
Similar to Cyber Security, HHS developed guidance for covered entities and business associates to better understand and respond to ransomware threats.
What is Ransomware?
Ransomware is malicious software known as malware that encrypts data such as files, folders and online accounts, locking an owner out and demanding a ransom in order to release the data. Other ransomware can destroy files.
Ransomware attacks occur thousands of times each day throughout the world.
Ransomware Security Measure Requirements
The HIPAA Security Rule requires implementation of security measures to help prevent ransomware, including
-Implementation of a security management process, including the conducting of a risk analysis for identifying threats and vulnerabilities to electronic protected health information (ePHI) and for implementing security measures to lessen those identified risks
-Implementation of procedures for guarding against and the detection of malicious software
-Training of users about malicious software protection so they can better assist in the detection of malicious software and understand how to report these detections
-Implementation of access controls for limiting access to ePHI to only those users or software programs with required access.
The Security Management Process standard of the Security Rule provides requirements for all covered entities and business associates to conduct a thorough and accurate risk analysis of potential risks and vulnerabilities to confidentiality, integrity and availability of all ePHI the entities create, receive, maintain, or transmit and to implement security measures sufficient to reduce those identified risks and vulnerabilities to a reasonable and appropriate level.
Covered entities and business associates will use this analysis to meet the standards and implementation specifications of the Security Rule and implement security measures to reduce specific risks and vulnerabilities to ePHI throughout the organization’s entire enterprise.
In general, the Security Rule simply establishes minimum requirements for the security of ePHI. Entities are encouraged to implement additional and more stringent security measures above what they determine to be required by Security Rule standards.
Recovering from Ransomware
The HIPAA Security Rule requires covered entities and business associates to implement policies and procedures that can assist an entity in responding to and recovering from a ransomware attack.
Maintaining frequent backups and ensuring the ability to recover data from backups is crucial to recovering from a ransomware attack, since ransomware denies access to data. Consider maintaining backups offline and unavailable from networks, as some ransomware can disrupt or remove online backups. The Security Rule requires the implementing a data backup plan for covered entities and business associates as part of maintaining a contingency plan.
Part of an entity’s contingency plan must include:
-Disaster recovery and emergency operations planning
-Analyze applications and data to ensure all necessary applications and data are accounted for
-Periodic testing of contingency plans to ensure the organizational is prepared to execute the plans and provide the confidence that they will be effective.
HIPAA requires Security incident procedures for responding to and the reporting of security incidents. Security incident procedures for responding to a ransomware attack should include processes for
-Detection of and conducting an initial analysis of the ransomware
-Containing the impact and propagation of the ransomware
-Eradicating the instances of ransomware and mitigating or remediating vulnerabilities that allowed the ransomware attack and propagation
Recovering from the ransomware attack by restoring data lost during the attack and returning to normal business operations
-Conducting post-incident activities, which could include a deeper analysis of the evidence to determine if the entity has any regulatory, contractual or other obligations as a result of the incident, such as providing a notification of a breach of protected health information. Lessoned learned should be incorporated into the overall security management process of the entity to further improve future security incident response effectiveness.
How to detect ransomware
HIPAA requires that an entity’s workforce receive appropriate security training, including training for detecting and reporting instances of malicious software, so as to assist entities in preparing their staff to detect and respond to ransomware. Indicators of a ransomware attack may include:
-Realization from a user that a file attachment was opened, a website was visited that may have been malicious, or a link that was clicked on.
-If a user is unable to access certain files, or files are being deleted, re-named or moved
-Detecting suspicious network communications between the ransomware and the attackers’ command and control servers, which would likely be detected by IT personnel through an intrusion detection solution.
Once a ransomware attack is discovered, the security incident response plan should be immediately activated. It should include measures to isolate the infected computer systems to minimize the attack.
HIPAA recommends entities infected with ransomware contact its local FBI or United States Secret Service field office, who work with Federal, state, local and international partners to assist victims of cybercrime and pursue cyber criminals globally.
Ransomware infected systems
The presence of ransomware on a covered entity’s or business associate’s computer systems is a security incident under the HIPAA Security Rule. A security incident is defined as the attempted or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with system operations in an information system. Once the ransomware is detected, the covered entity or business associate must initiate its security incident and response and reporting procedures.
An entity’s security incident response activities should begin with an initial analysis to determine
-The scope of the incident to identify what applications, systems and networks are affected
-A detailed origination of the incident
-If the incident is finished, is ongoing or has propagated additional incidents throughout the environment
-A detailed look at how the incident occurred. For example, the vulnerabilities exploited and the tools and attack methods used.
Later security incident response activities should include steps to
-Contain the impact and propagation of the ransomware
-Eradicate the instances of ransomware and mitigate or remediate vulnerabilities that permitted the ransomware attack and propagation
-Recover from the ransomware attack by restoring data lost during the attack and returning to “business as usual” operations
-Conduct post-incident activities, which could include a deeper analysis of the evidence to determine if the entity has any regulatory, contractual or other obligations as a result of the incident (such as providing notification of a breach of protected health information), and incorporating any lessons learned into the overall security management process of the entity to improve incident response effectiveness for future security incidents
A deeper analysis should involve assessing whether or not there was a breach of PHI as a result of the security incident. The presence of ransomware (or any malware) is a security incident under HIPAA that may also result in an impermissible disclosure of PHI in violation of the Privacy Rule and a breach, depending on the facts and circumstances of the attack.
To demonstrate that there is a low probability that the protected health information (PHI) has been compromised because of a breach, a risk assessment considering at least the following four factors must be conducted
- Nature and extent of the PHI involved, including the types of identifiers and the likelihood of re-identification
- The unauthorized person who used the PHI or to whom the disclosure was made
- If the PHI was actually acquired or viewed
- Extent to which the risk to the PHI has been mitigated
A thorough and accurate evaluation of the evidence acquired and analyzed as a result of security incident response activities could help entities with the risk assessment process above by revealing, for example
-the exact type and variant of malware discovered
-the algorithmic steps undertaken by the malware; communications, including exfiltration attempts between the malware and attackers’ command and control servers
-If the malware propagated to other systems, potentially affecting additional sources of electronic PHI. Correctly identifying the malware involved can assist an entity to determine what algorithmic steps the malware is programmed to perform.
Understanding what a particular strain of malware is programmed to do can help determine how or if a particular malware variant may laterally propagate throughout an entity’s enterprise, what types of data the malware is searching for, whether or not the malware deposits hidden malicious software or exploits vulnerabilities to provide future unauthorized access, among other factors.
While entities are required to consider the four factors listed above in conducting their risk assessments to determine whether there is a low probability of compromise of the ePHI, entities are encouraged to consider additional factors, as necessary, to appropriately evaluate the risk that the PHI has been compromised. If, for example, there is a high risk of the unavailability of the data, or high risk to the integrity of the data, such additional factors may indicate compromise. In those cases, entities must provide notification to individuals without unreasonable delay, particularly given that any delay may impact healthcare service and patient safety.
The entity may wish to consider the impact of the ransomware on the integrity of the PHI. Ransomware, after encrypting the data it was seeking, may delete the original data and leave only the data in encrypted form. An entity may be able to show mitigation of the impact of a ransomware attack affecting the integrity of PHI through the implementation of robust contingency plans including disaster recovery and data backup plans.
Conducting frequent backups and ensuring the ability to recover data from backups is crucial to recovering from a ransomware attack and ensuring the integrity of PHI affected by ransomware. Test restorations should be periodically conducted to verify the integrity of backed up data and provide confidence in an organization’s data restoration capabilities. Integrity to PHI data is only one aspect when considering to what extent the risk to PHI has been mitigated.
The risk assessment to determine whether there is a low probability of compromise of the PHI must be thorough and reach conclusions that are reasonable given the circumstances. Covered entities and business associates must also maintain supporting documentation sufficient enough to meet their burden of proof regarding the breach assessment, including:
-Documentation of the risk assessment demonstrating the conclusions reached
-Documentation of any exceptions determined to be applicable to the impermissible use or disclosure of the PHI
-Documentation demonstrating that all notifications were made if a determination was made that the impermissible use or disclosure was a reportable breach.
Cybersecurity Framework
NIST (National Institute of Standards and Technology) released the Framework for Improving Critical Infrastructure Cybersecurity (Cybersecurity Framework) in 2014.
The Cybersecurity Framework provides a voluntary, risk-based approach using existing guidelines, practices and standards to better assist organizations across all industries to communicate, manage and understand cybersecurity risks.
In the health care industry, covered entities and business associates) regulated by the Health Insurance Portability and Accountability Act (HIPAA) must comply with the HIPAA Security Rule to ensure the availability, confidentiality and integrity of electronic protected health information (ePHI) that they create, maintain, receive and/or transmit.
For a starting place to identify potential gaps in your program, review the table in the link here, beginning on page 3, which identifies “mappings” between the Cybersecurity Framework and the HIPAA Security Rule.
Addressing gaps can strengthen compliance with the Security Rule and improve the ability to secure ePHI and other critical information and business processes. As an example, if a covered entity has an existing security program aligned to the HIPAA Security Rule, the entity can use this mapping document to identify which pieces of the NIST Cybersecurity Framework it is already meeting and which represent new practices to incorporate into its risk management program.
In addition, the document allows organizations to communicate activities and outcomes both internally and externally with regard to their cybersecurity program by utilizing the Cybersecurity Framework as a common language.
The mapping can also be combined with similar mappings to account for additional organizational considerations such as privacy, regulation and legislation.
Cyber Awareness Newsletters
OCR switched to quarterly cybersecurity newsletters in 2019. The purpose of the newsletters is to help HIPAA covered entities and business associates maintain compliance with the HIPAA Security Rule by identifying emerging or prevalent issues, and highlighting best practices to safeguard PHI.
You may sign up for their Cyber Awareness Newsletter Here
(https://list.nih.gov/cgi-bin/wa.exe?SUBED1=OCR-SECURITY-LIST&A=1)
HIPPA Section 12
HIPAA Enforcement and Audits
What is HIPAA Enforcement?
Enforcement Rule
The HHS Office for Civil Rights is in charge of enforcing both the Privacy and Security Rule. Enforcement of the Privacy Rule started April 14, 2003 for most HIPAA covered entities. Since its inception, OCR's enforcement activities have obtained significant results that improved the privacy practices of covered entities. Corrective actions obtained by OCR from covered entities have resulted in systemic changes that have improved the privacy protection of health information for all individuals they serve.
HIPAA covered entities are required to comply with the Security Rule, which OCR, a law enforcement agency that does not generally release their pending investigation information to the public, is responsible for enforcing.
Enforcement Process
OCR enforces the Privacy and Security Rules in a number of ways:
-Investigation of complaints filed with OCR
-Conducting of compliance reviews to determine if covered entities are in compliance
-Performing of education and outreach to foster compliance with the Rules' requirements
OCR also works with the Department of Justice, referring potential criminal violations of HIPAA.
Resolution Agreements and Civil Penalties
A resolution agreement is a settlement agreement that is signed by HHS and a covered entity or business associate where the covered entity or business associate agree to perform specific obligations and make reports to HHS, normally for a period of three years. HHS monitors the covered entity’s compliance with the specific obligations during this time. Resolution agreements can include the payment of a resolution amount.
Civil money penalties (CMP) may be imposed for noncompliance against a covered entity if HHS cannot reach a satisfactory resolution through the covered entity’s demonstrated compliance or corrective action through other informal means, such as a resolution agreement.
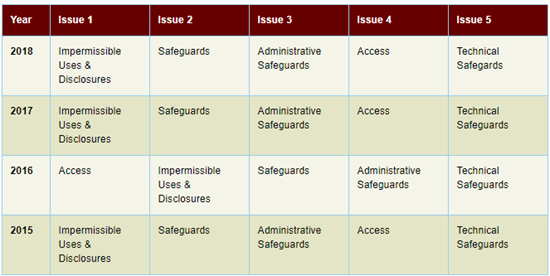
The above table shows the top five issues in investigated cases that were closed with corrective action over the last 4 years, per HHS.
Audits

HIPAA established important national standards for the privacy and security of protected health information, and the Health Information Technology for Economic and Clinical Health Act (HITECH) established breach notification requirements to provide greater transparency for individuals whose information may be at risk.
HITECH requires the HHS Office for Civil Rights (OCR) to conduct periodic audits of covered entity and business associate compliance with the HIPAA Privacy, Security, and Breach Notification Rules.
This includes reviewing by OCR of policies and procedures adopted and employed by covered entities and their business associates to meet certain standards and implementation specifications of the Privacy, Security, and Breach Notification Rules.
OCR is developing enhanced protocols to be used in the next round of audits. OCR is also pursuing a new strategy to test the efficacy of desk audits in evaluating the compliance efforts of the HIPAA regulated industry.
Program goals
The audits are an opportunity for OCR to identify best practices, examine mechanisms for compliance, uncover new risks and vulnerabilities in addition to OCRs ongoing complaint investigations and compliance reviews, and enable OCR to work to resolve problems before they result in breaches.
OCR identifies best practices through the process of the audit and then provides guidance to identified compliance challenges.
Will your organization be selected for an audit?
All covered entities and business associates are eligible for an audit.
How are auditees selected?
The OCR is identifies pools of covered entities and business associates across a wide range of health care providers, health plans, health care clearinghouses and business associates. This allows OCR to assess HIPAA compliance across the industry considering size, types and operations of potential auditees. Possible criteria for auditee selection includes affiliations with other healthcare organizations, geographic factors, if an organization is public or private, size of the entity, type of entity and its relationship to individuals, and present enforcement activity with OCR.
Note that the OCR will not audit entities who have an open complaint investigation or who are in the process of a compliance review.
Selection Process
The OCR will send a questionnaire to covered entities and business associates to gather data about the operations, size and type of potential auditees. The data is then used with other information to create pools of potential auditees in order to make audit subject selections.
OCR asks covered entity auditees for a list of their business associates along with contact information.
The selection process is random.
If a covered entity or business associate fails to respond to information requests, OCR will use publically available information about the entity to create its audit pool. An entity that does not respond to OCR may still be selected for an audit or subject to a compliance review.
About the Audit Program
Audits will examine compliance with specific requirements of the Privacy, Security, or Breach Notification Rules.
If an entity does not respond to OCR’s requests for information, OCR will use publicly available information about the entity to create its audit pool. Entities who do not respond to OCR can still be selected for an audit or subject to a compliance review.
Audit Timeline
Covered entities will be notified by OCR in writing via email about their selection for a desk audit (covered entities) or onsite audit (covered entities and business associates.)
For desk audits:
-The email will introduce the audit team, explain the process and discuss OCRs expectations in detail.
-The email will also include initial requests for documentation. Requested information should be submitted electronically through OCR’s secure portal within 10 business days of the date identified in the information request.
-The auditor will then review the information submitted and provide the auditee with draft findings.
Auditees will then have 10 business days to review and return written comments to the auditor, if required.
The auditor will then complete a final audit report for each entity within 30 business days after the auditee’s response. The final report will be shared with the audited entity.
For onsite audits:
-The auditors will schedule an entrance conference and provide more information about the onsite audit process including expectations for the audit.
-The onsite audit will be conducted over three to five days, based on the size of the entity.
-Onsite audits are more comprehensive than desk audits, covering a wider range of requirements from the HIPAA Rules.
-Entities will have 10 business days to review and provide written comments to the auditor draft findings.
-The auditor will complete a final audit report for each entity within 30 business days after the auditee’s response, and share the final report with the audited entity.
After an audit
-OCR uses the information from all audits to develop tools and guidance to assist the industry in compliance self-evaluation and in preventing breaches.
- OCR may initiate a compliance review to further investigate if an audit report indicates a serious compliance issue.
-OCR does not make audit information public unless it is requested and required under the Freedom of Information Act (FOIA).
HIPPA Section 13
What is a breach?

A breach is an impermissible use or disclosure under the privacy rule that compromises the security or privacy of the PHI.
Common breaches include:
-Faxed PHI to the wrong place
-Inappropriate access due to violating the minimum necessary standard
-Patient receiving the wrong patient information
When determining a breach, consider:
-What was the PHI that was disclosed?
-Who was it disclosed to?
For example, a Doctor’s Office, and if so, who was the person(s) at the office who received it?
-Was the information viewed or acquired?
-How has the patient information that was breached mitigated?
As another example, if PHI was faxed to wrong office, ask the office the information was incorrectly sent to, to shred the information. Make all reasonable efforts to recover the document(s) if it was sent to the wrong person.
What is Mandatory Breach Response and Notification?
The Breach Notification Rule
HIPAAs Breach Notification Rule requires HIPAA covered entities and their business associates to provide notification after a breach of unsecured protected health information.
The HITECH Act has similar breach notification provisions that are enforced by the Federal Trade Commission (FTC). They apply to vendors of personal health records and their third party service providers.
Definition of Breach
A breach is an impermissible use or disclosure under the Privacy Rule that compromises the privacy or security of the PHI. An impermissible use or disclosure of PHI is presumed to be a breach unless the appropriate covered entity or business associate can demonstrate there is a low probability that the PHI was compromised based on a risk assessment of at minimum:
-The nature and extent of the PHI involved, including the types of identifiers and the likelihood of re-identification
-The unauthorized person who used the PHI or who the disclosure was made to
-If the PHI was acquired or only viewed
-The extent to which the risk to the PHI has been mitigated
Where applicable, covered entities and business associates have discretion to provide the required breach notifications after an impermissible use or disclosure without performing a risk assessment to determine the probability that the PHI has been compromised.
There are 3 exceptions to the definition of a breach
1 - Unintentional access, acquisition, or use of PHI by a workforce member or person acting under the authority of a covered entity or business associate, provided it was made in good faith within the scope of authority.
2 - Inadvertent disclosure of PHI by a person authorized to access PHI at a covered entity or business associate to another person authorized to access PHI at the covered entity or business associate, or organized health care arrangement where the covered entity participates. The information cannot be further used or disclosed in a way that is not permitted by the Privacy Rule in these cases.
3 - A good faith belief by the covered entity or business associate that the unauthorized person who the impermissible disclosure was made to would not have been able to retain the information.
Unsecured Protected Health Information and Guidance
Covered entities and business associates are required to only provide the required notifications if the breach involved unsecured PHI. Unsecured PHI is PHI that is deemed usable, readable, or decipherable to unauthorized persons through the use of a technology or methodology specified by the Secretary in guidance.
The guidance specifies encryption and destruction as the technologies and methodologies for rendering PHI unusable, unreadable, or indecipherable to unauthorized individuals. It also applies to unsecured personal health record identifiable health information under FTC regulations. Covered entities, business associates, and also entities regulated by the FTC regulations, that secure information as specified by the guidance are not required to provide notifications in the event of a breach of this information.
Breach Notification Requirements
Covered entities must provide notification of a breach of unsecured PHI to affected individuals, the Secretary, and to the media in certain circumstances. Business associates must notify covered entities if a breach occurs at or by the business associate.
Individual Notice
Upon discovery of a breach of unsecured PHI, covered entities must provide the affected individual(s) notice in written form by first-class mail, or via e-mail if the affected individual has agreed to receive these notices electronically. The covered entity is required to post the notice on its website homepage for a minimum of 90 days, or provide the notice in major print or broadcast media where the affected individuals likely reside, if the covered entity has insufficient or out of date contact information for 10 or more individuals.
The covered entity must include a toll free phone number that remains active for a minimum of 90 days so individuals can find out if their information was involved in the breach.
The covered entity may provide substitute notice by an alternative form of written notice, by telephone, or other means if the covered entity has insufficient or out-of-date contact information for fewer than 10 individuals.
The individual notifications are required to be provided without unreasonable delay and no later than 60 days of the discovery of a breach. They must include a brief description of:
-The breach
-The types of information that were involved in the breach
-The steps affected individuals should take to protect themselves from potential harm
-What the covered entity is doing to investigate the breach, mitigate the harm, and prevent further breaches
Contact information for the covered entity and/or business associate must also be included.
For breaches at or by a business associate, though the covered entity is responsible for ensuring individuals are notified, the covered entity can delegate responsibility of providing individual notices to the business associate.
Media Notice
Covered entities who experience a breach affecting more than 500 residents of a State or jurisdiction are also required to provide notice to prominent media outlets serving the State or jurisdiction. Covered entities can provide the notification through a press release to appropriate media outlets serving the affected area.
This media notification needs to be provided without unreasonable delay and no later than 60 days following the discovery of a breach. It is required to include the same information required for the individual notice.
Notice to the Secretary
Covered entities are required to notify the Secretary of breaches of unsecured PHI, in addition to notifying affected individuals and the media, if required. The Secretary can be notified by visiting the HHS web site, filling out a breach report form and electronically submitting it.
Covered entities must notify the Secretary without unreasonable delay and no later than 60 days following a breach if 500 or more individuals are affected.
The secretary is to be notified of breaches affected less than 500 individuals on an annual basis and no later than 60 days from the end of the calendar year that the breaches were discovered in.
The covered entity should provide an estimate if the number of individuals affected by a breach is unknown at the time of submission. Updates can be submitted if additional information is discovered.
If only one option is available (over 500 individuals or under 500 individual) the covered entity should pick the best option and explain the details of the number of affected individuals if there is an option to type additional information.
Additional information can be added, and current information edited, for previously submitted notices to the Secretary, as it is discovered.
Notification by a Business Associate
Business associates are required to notify the covered entity without unreasonable delay and no later than 60 days from the discovery of a breach of unsecured PHI occurring at or by a business associate.
Business associates should provide the covered entity with the identification of the individual(s) affected by the breach and also any other available information required to be provided by the covered entity in its notification to affected individuals.
Administrative Requirements and Burden of Proof
Covered entities and business associates, as applicable, must be able to demonstrate all required notifications were provided or that a use or disclosure of unsecured PHI did not constitute a breach.
Regarding impermissible use or disclosure, a covered entity and/or business associate must maintain documentation that all required notifications were made or maintain documentation that shows notification was not required. These can include:
-The risk assessment showing a low probability that the PHI has been compromised by the impermissible use or disclosure
-The application of any other exceptions to the definition of breach.
Covered entities are also required to comply with certain administrative requirements with respect to breach notification. As examples, covered entities must:
-Have written policies and procedures regarding breach notification
-Train employees on these policies and procedures
-Develop and apply appropriate sanctions against workforce members who do not comply with these policies and procedures.
Breach Reporting
To report a breach within an organization, the Breach risk assessment will be filled out and then taken directly to HIPAA Compliance Officer.
Submitting Notice of a Breach to the Secretary
If a covered entity discovers a breach of unsecured PHI, it must notify the Secretary using the Secretary’s web portal.
Reports to Congress
As part of the HITECH Act, reports containing the number and nature of breaches reported along with the actions taken in response to those breaches, are compiled by Secretary of HHS and made available to the public on the HHS website.
HIPPA Section 14
How does HIPAA affect marketing?

History
The HIPAA Privacy Rule provides individuals with important control over if and how their PHI is used and disclosed for marketing purposes.
The Rule requires an individual’s written authorization before a use or disclosure of his or her PHI is used for marketing, with limited exceptions. To not interfere with core health care functions, the Rule distinguishes marketing communications from those communications about goods and services that are essential for quality health care.
How the Rule Works
The Privacy Rule addresses the use and disclosure of PHI for marketing purposes by the following:
-Defining what is “marketing” under the Rule
-Excepting from that definition certain treatment or health care operation activities
-Requiring individual authorization for all uses or disclosures of PHI for marketing purposes with limited exceptions.
What is considered marketing under HIPAA?
The HIPAA Privacy Rule defines marketing as making a communication about a product or service that encourages recipients of the communication to purchase or use the product or service. If the communication is marketing, the communication can happen only if covered entities obtain the individual’s authorization prior to marketing. There are exceptions.
Examples of marketing that require prior authorization are communication from a:
-Health insurer promoting insurance offered by the same company.
-Hospital informing former patients about a facility that is not part of the hospital who charges fees to provide services to what the patient may benefit from, but not for the purpose of providing treatment advice.
Marketing is also identified as an arrangement between a covered entity and any other entity where the covered entity discloses PHI in exchange for direct or indirect compensation for the other entity or its affiliate to make communication to the individual about their product or service that encourages those individual to purchase or use the product or service.
Before these marketing communications occur, the individual must authorize them. In other words, a covered entity cannot sell PHI, not even lists of patients, to a business associate or third party, without first obtaining authorization from each individual.
Marketing examples include:
-A health plan sells a list of its members to a company that intends to send the plans’ members brochures on the benefits of purchasing and using its product.
-A drug manufacturer receives a list of patients from a covered health care provider and then uses that list to send discount coupons to those patients.
What is not marketing?
The Privacy Rule lists exceptions to marketing under 3 categories. Communications are not marketing if the communication is made:
1 – To describe a health-related product, service, or payment for the product or service that is provided by or included in a plan of benefits of the covered entity making the communication. These include:
-The entities participating in a health care provider network or health plan network are replacing or enhancing the health plan
-Health-related products or services are available to a health plan enrollee that add value to, but are not part of a plan of benefits.
Communications by a covered entity about its products and services is permitted when, for example, a new department or new equipment is acquired, or information including application forms for a Medicare supplemental plan when an individual approaches Medicare age eligibility.
2 – For treatment of the individual, including:
-A pharmacy or other health care provider mailing prescription refills reminders, or contracting with a mail house to do so.
-A primary care physician referring individuals to a specialist for follow-up tests or providing free samples of a prescription drug to patients.
3 - For case management or care coordination for the individual or to direct or recommend alternative treatments or health care providers to individuals, including:
-A doctor shares patient medical records with behavior management programs to find out which program best suits the patient.
-A hospital social worker shares medical record information with a nursing home when recommending the patient be transferred from hospital bed to nursing home.
The activity must allowed under the Privacy Rule for the above examples. Business Associates may be utilized to make these communications provided they agree to use PHI for communication activities of the covered entities only.
Marketing Authorizations and when authorizations are not necessary.
Communication that meets the definition of marketing is not permitted without first receiving authorization from the individual.
A marketing communication does not require an authorization if it is communicated face-to-face by a covered entity to an individual. Examples include:
-Insurance agents selling health insurance policies to an individual and offers additional insurance policies.
-Hospital providing free product specific to the department the individual visited.
HIPPA Section 15
Managing and Resolving HIPAA Complaints

Healthcare providers must be ready to handle HIPAA privacy complaints from patients. Policies must be developed that cover procedures to follow for complaints, and staff need to be trained to deal with HIPAA privacy complaints correctly, in order to provide an effective response.
Patients need to be clearly informed, through a Notices of privacy practices, for example, about how they can file HIPAA privacy complaints when they feel their privacy was violated or if they feel the HIPAA Rules have been breached.
Patients must be asked to submit complaints in writing using a pre made form from your establishment, in the event a verbal complaint is made. Once completed and submitted by the patient, the form should be sent to the Privacy Officer to investigate.
Investigate All Complaints and Take Prompt Action
When investigating a HIPAA privacy complaints, identify all persons and parties involved and also how the patient privacy was violated to ensure the breach is not a one-time issue but rather a more widespread organization problem. The Privacy Officer will determine the privacy violation cause and action to take so that all issues are corrected to prevent similar future breaches from occurring. Company policies and procedures would need to be updated if new information is discovered that will help to prevent privacy violations.
Additionally, the individuals involved in the breach face disciplinary action from training to loss of employment. If a crime is suspected, law enforcement should receive the incident report.
The Privacy Officer will determine if there was a HIPAA breach and if the incident needs to be reported. If other patients are may have had their privacy violated, those patients must be notified within 60 days.
A HIPAA Privacy Complaint is a serious matter and should be dealt with quickly and efficiently. Moving to action will also show the patient the seriousness and important all potential privacy and security violations are. The outcome of the complaint investigation should be that the problem has been addressed to make sure it will not happen again, reassurance to the patient that any risks have been mitigated, and a sincere apology.
Below is a summary of how to deal with a HIPAA complaint
-Ask the patient to submit the HIPAA privacy complaint in writing
-Send the compliant to the Privacy Officer
-The Privacy Officer will find out all involved and the PHI that was breached
-The main cause of the breach
-Take action to mitigate harm
-Send information to HR for disciplinary action against employees, if necessary
-Send the breach report to law enforcement, if necessary
-Update policies and procedures to prevent a recurrence
-Staff should be retrained
-Understand if the breach is a reportable incident
-Collect and organize all pertinent documentation with regard to the breach and to the investigation
-Speak with the person or persons who made the complaint to explain the results of the investigation
HIPPA Section 16
What Documentation is required under HIPAA?

Below is a list of the documentation required under the Security Standard:
Security Management Process
-Risk Analysis
-Risk Management
-Sanction Policy
-Information System Activity Review
Assigned Security Responsibility
Workforce Security
-Authorization and/or Supervision
-Workforce Clearance Procedure
-Termination Procedures
Information Access Management
-Isolating Healthcare Clearinghouse Functions
-Access Authorization
-Access Establishment and Modification
Security Awareness and Training
-Security Reminders
-Protection from Malicious Software
-Log-in Monitoring
-Password Management
Security Incident Procedures
-Response and Reporting
Contingency Plan
-Data Backup Plan
-Disaster Recovery Plan
-Emergency Mode Operation Plan
-Testing and Revision Procedures
-Applications and Data Criticality Analysis
Evaluation
Business Associate Contracts and other arrangements
-Written Contract and Other Arrangement
Facility Access Controls
-Contingency Operations
-Facility Security Plan
-Access Control and Validation Procedures
-Maintenance Records
Workstation Use
Workstation Security
Device and Media Controls
-Disposal
-Media Re-use
-Accountability
-Data Backup and Storage
Access Control
-Unique User Identification
-Emergency Access Procedure
-Automatic Logoff
-Encryption and Decryption
Audit Controls
Integrity
-Mechanism to Authenticate Electronic Protected Health Information
Person or Entity Authentication
Transmission Security
-Integrity Controls
-Encryption
Business Associate or other arrangements
-Business Associate Contracts
-Other arrangements
Requirements for Group Health Plans
-Implementation Specifications
Policies and Procedures
Documentation
-Time Limit
-Availability
-Updates
Additional documentation under HIPAA includes:
-Firewall configurations, the systems they apply to, who has access to them, if they are up-to-date
-FTP usage and configuration
-Efficiency of all processes
-Role-based access levels
-PHI location documentation
-Notice of Privacy Practices
-Third party risks – confirmation that there are none
-Software development lifecycles
-Identified vulnerabilities and how your system is reacting to each
-Incident response plan/breach response plan
-Current and future goals and milestones
-Status of unimplemented addressable implementation standards
-Work area procedures
-Training logs
-List of authorized wireless access points
-List of all devices including physical location, serial numbers, and make/model
-All contracts and agreements
-Lists of vendors
-Employee handbook
HIPPA Section 17
Cloud Computing and Social Media
Cloud Computing

If a covered entity engages the services of a Cloud Service Provider (CSP) to create, maintain, receive, or transmit ePHI on the covered entities behalf, the CSP becomes a business associate under HIPAA.
This is the case when a CSP processes or stores only encrypted ePHI and lacks an encryption key for the data.
Not having an encryption key does not exempt a CSP from a status of business associate under the HIPAA Rules.
The covered entity or business associate and CSP must enter into a HIPAA compliant business associate agreement (BAA). The CSP is then contractually liable for meeting the terms of the BAA and also for compliance with the applicable requirements of the HIPAA Rules.
Digital Media and Social Networking issues
With the rise of social media networks like Facebook, HIPAA laws are continuously being updated to address growing technology. HIPAA requirements do exist that apply to social media to reduce privacy violation risks.
Social media provides benefits including the ability for healthcare organizations to interact with patients and more involvement with their health. While it simplifies the process for healthcare providers communicating urgent messages, the potential for HIPAA Rules and patient privacy to be violated exists.
HIPAA and Social Media

The HIPAA Privacy Rule prohibits the use of PHI on social media networks. That includes any text about specific patients as well as images or videos that can result in a patient being identified. PHI can only be included in social media posts if a patient has given their consent in writing to allow their PHI to be used and then only for the purpose(s) specifically mentioned on their consent form.
Social media channels can be used for biographies of an organization’s staff, event details, health tips, marketing messages and medical research. All of this is acceptable under HIPAA provided no PHI is included in the posts.
Employees need to be thoroughly trained regarding HIPAA Social Media Rules to avoid violations occurring. This training should occur prior to employment and then annually.
Social Media HIPAA Violations include:
-Photo, text and/or video posts (publicly or in a private group) of patients and/or their PHI without written consent from the patient.
-Gossip posts about patients.
-Informational posts that can be identifiable to an individual.
-Photographs or image sharing that were taken within a healthcare facility where patients and/or PHI can be seen.
HIPAA Social Media guidelines to follow
-Social media accounts should be part of the organization’s risk assessment.
-Communicating penalties for social media HIPAA violations including criminal penalties, loss of license and termination.
-Annual social media policy reviewing and updating.
-Ensuring approval by your compliance department for new usage of social media sites.
-Providing examples to staff of acceptable and not acceptable social media behavior.
-Development of policies and procedures regarding the use of social media for marketing. This should include in detail the process of how marketing occurs on social media.
-Prior to posting, all social media posts should be internally reviewed and approved by legal or compliance departments.
-Automating the flagging of potential HIPAA violations can be accomplished to aid in the monitoring of social media accounts and communications.
-Have in place clear policies about social media use and make sure all employees are aware of how HIPAA relates to social media platforms.
-Person social media accounts should be separated from business social media accounts.
-Training of all staff on suitable social media use as part of HIPAA training and conduct the proper refresher training on an annual basis. This should include the need for staff to report any potential HIPAA violations.
-Security needs to be built in to prevent unauthorized access of business social media accounts.
Congratulations!
You have completed the HIPAA Training portion of the Course.
Please proceed to Testing.
Testimonials
Individual
"Thanks for the fast service! I needed my certification before I could begin my new job. I was able to complete the test and print my certificate in time to start work Monday morning." Janet F., Orlando, FL.
Company
"Over 200 employees throughout our offices are required to complete Blood borne Pathogen Certification annually. Employee availability and scheduling conflicts made it nearly impossible to schedule an onsite class. We were pleased to learn that our OSHA requirements can be satisfied online. Looking forward to the ease of use next year." Mary M., Cardinal Health
Follow Us
Contact Us
Have a question? Customer service representatives are standing by to assist.

